Mobile App Permissions Guide: What Apps Can Really Access
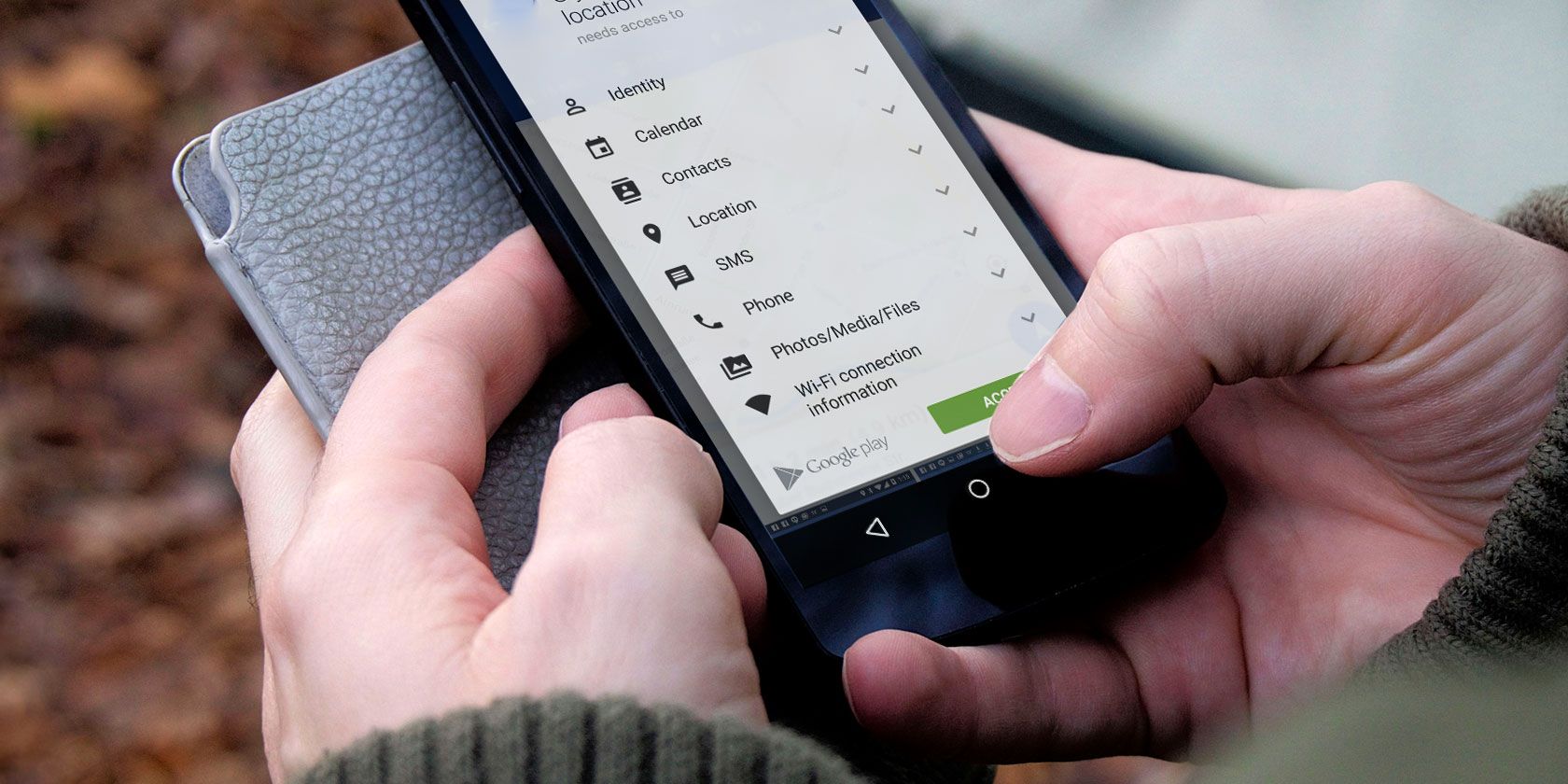
Ever downloaded a seemingly innocent flashlight app, only to wonder why it needs access to your contacts? You're not alone. In today's app-filled world, understanding what permissions you're granting is crucial to protecting your privacy and security.
It's easy to click "Allow" without a second thought, especially when you're eager to use a new app. However, giving apps excessive permissions can expose sensitive information, like your location, contacts, photos, and even microphone and camera access. This can lead to unwanted data collection, targeted advertising, or, in worst-case scenarios, security breaches and privacy violations.
This guide aims to demystify mobile app permissions. We'll explore the types of permissions apps request, what they actually allow the app to do, and how you can manage these permissions to safeguard your personal data. We'll break down the jargon and provide practical tips to help you make informed decisions about the apps you use.
In this guide, we'll shed light on the various types of app permissions, delve into the potential risks associated with granting excessive access, provide practical tips for managing permissions on both Android and i OS devices, and address common misconceptions about app privacy. By understanding these concepts, you can confidently navigate the app ecosystem and protect your valuable personal information.
Understanding Common App Permissions
The goal of this section is to give you a clear understanding of the most frequently requested app permissions and what they enable apps to do. We aim to provide simple explanations, moving beyond technical jargon, so you can confidently assess the potential impact of granting each permission.
I remember once downloading a photo editing app that asked for access to my contacts. It seemed completely unnecessary, and it immediately raised a red flag for me. Why would a photo editor need my contacts? It made me realize how easily we can blindly grant permissions without really considering the implications. After that, I started paying much closer attention to what apps were requesting. Common permissions include access to your camera (allowing the app to take photos and videos), microphone (enabling the app to record audio), location (granting access to your device's GPS coordinates), contacts (allowing the app to view and modify your contact list), storage (permitting the app to read and write files on your device), and network access (allowing the app to connect to the internet). Each of these permissions can be used legitimately, but they also have the potential for misuse if an app is poorly designed or intentionally malicious. For instance, a weather app legitimately needs your location to provide accurate forecasts, but a game might not need access to your camera. Understanding the purpose behind each permission request is key to making informed decisions about what to allow.
The Risks of Granting Excessive Permissions
This section clarifies the potential dangers of allowing apps more access than they truly need. We'll cover scenarios like data collection, targeted advertising, and even potential security vulnerabilities that can arise from granting broad permissions.
Granting excessive permissions to apps can open the door to a range of privacy and security risks. One major concern is data collection. Many apps collect user data for various purposes, including targeted advertising, analytics, and even selling data to third parties. The more permissions an app has, the more data it can potentially collect about you. For example, an app with access to your location, contacts, and browsing history can build a detailed profile of your habits, interests, and social connections. This information can then be used to personalize ads, track your movements, or even discriminate against you based on your demographics. Another risk is the potential for security vulnerabilities. If an app has access to sensitive data like your camera, microphone, or storage, it could be exploited by hackers or malicious actors. A compromised app could be used to eavesdrop on your conversations, steal your photos and videos, or even gain access to your device's operating system. Moreover, even if an app is not intentionally malicious, poorly designed apps with excessive permissions can drain your battery, slow down your device, and consume your data allowance unnecessarily. Therefore, it's crucial to carefully review the permissions requested by each app and only grant access to the features that are absolutely necessary for the app to function properly.
The History and Myths of App Permissions
The aim is to provide a brief history of app permissions, highlighting how they've evolved over time, and to debunk common myths and misconceptions surrounding app permissions and data privacy.
The concept of app permissions has evolved significantly since the early days of mobile operating systems. Initially, app permissions were often all-or-nothing, meaning users had to grant all requested permissions or not install the app at all. This approach lacked granularity and often forced users to make uncomfortable choices. Over time, operating systems like Android and i OS have introduced more granular permission models, allowing users to grant or deny individual permissions. This has given users more control over their data and privacy. However, many myths and misconceptions still surround app permissions. One common myth is that all apps are trustworthy and only request permissions they truly need. In reality, many apps request excessive permissions for various reasons, including data collection and targeted advertising. Another myth is that denying permissions will always break an app. While some permissions are essential for an app to function, many others are optional and can be safely denied without affecting the app's core functionality. Finally, some people believe that app permissions are only relevant for free apps. However, even paid apps can request excessive permissions and collect user data. Therefore, it's important to be vigilant about app permissions regardless of whether an app is free or paid. By understanding the history and debunking the myths surrounding app permissions, users can make more informed decisions about their data and privacy.
Hidden Secrets of App Permissions
This section uncovers less obvious aspects of app permissions, such as how apps can sometimes use permissions in ways that aren't immediately apparent and how permission settings can interact with each other.
While the basic function of app permissions seems straightforward, there are several hidden aspects that users should be aware of. One such secret is the way apps can leverage combined permissions. For instance, an app with access to your location and contacts can infer your social connections and daily routines based on where you are and who you're with. This type of combined information can be surprisingly revealing. Another hidden aspect is that some apps can access data indirectly through other apps. If one app on your device has broad permissions, it could potentially share data with other apps, even if those apps don't have the same permissions directly. Furthermore, some apps may use workarounds to access data without explicitly requesting permission. For example, an app can analyze your device's sensors, like the accelerometer or gyroscope, to infer your activity level without requesting permission to track your location. It is also often the case that the wording of permission requests can be misleading or vague. Some apps use technical jargon or ambiguous language to obscure the true purpose of a permission. Finally, the default permission settings on your device can also influence how apps behave. Many devices have default settings that automatically grant certain permissions to apps, making it easy for users to overlook them. By understanding these hidden secrets of app permissions, users can gain a deeper understanding of how their data is being accessed and used.
Recommendations for Managing App Permissions
This section provides practical advice on how to effectively manage app permissions on both Android and i OS devices. We'll cover how to review existing permissions, how to grant or deny permissions, and how to use built-in privacy settings to limit data collection.
Managing app permissions effectively is crucial for protecting your privacy and security on mobile devices. The first step is to regularly review the permissions you've granted to each app. On both Android and i OS, you can access a list of apps and their permissions in the device's settings. Take the time to go through this list and identify any apps that have excessive or unnecessary permissions. If you find an app with permissions that don't seem relevant to its functionality, consider denying those permissions or uninstalling the app altogether. When granting permissions, be mindful of the principle of least privilege. Only grant permissions that are absolutely necessary for the app to function properly. If an app requests a permission that seems suspicious or unnecessary, deny it. In many cases, the app will still work, albeit with limited functionality. Both Android and i OS offer built-in privacy settings that allow you to limit data collection. For example, you can restrict location tracking, disable ad personalization, and control which apps have access to your microphone and camera. Take advantage of these settings to further protect your privacy. Finally, be aware of the "while using the app" permission option. This option allows apps to access certain features only when you're actively using the app. This can be a good compromise between granting full access and denying access altogether. By following these recommendations, you can take control of your app permissions and protect your data from unwanted access.
Understanding "Normal" vs. "Dangerous" Permissions
Android categorizes permissions into different protection levels, including "normal" and dangerous.Normal permissions pose little risk to the user's privacy, while dangerous permissions can potentially access sensitive data. It's important to understand these distinctions to prioritize which permissions to review and manage carefully.
Android’s permission model categorizes permissions into groups based on the potential risk they pose to the user. "Normal" permissions are those that pose little to no risk to the user’s privacy or security. These permissions typically involve accessing resources that are already publicly available or don't reveal sensitive information. For example, access to the device's internet connection or the ability to set the device's time zone are considered normal permissions. Apps are automatically granted these permissions at install time, and users are not prompted to explicitly grant them. "Dangerous" permissions, on the other hand, are those that can potentially access sensitive user data or control features that could affect the user’s privacy or security. These permissions require explicit user consent before they can be granted. Examples of dangerous permissions include access to the device's camera, microphone, location, contacts, and storage. When an app requests a dangerous permission, the user is presented with a dialog box asking them to allow or deny the permission. It’s important to carefully consider the implications of granting dangerous permissions before making a decision. Apps should only request dangerous permissions that are absolutely necessary for their core functionality. If an app requests a dangerous permission that seems suspicious or unnecessary, it's best to deny it. Android also includes other permission groups, such as "signature" and "signature Or System," which are used for special cases and typically require the app to be signed by the same certificate as the system or a trusted vendor.
Tips for Secure App Downloads
The goal of this section is to provide guidance on how to minimize risks when downloading new apps. We'll cover topics like checking app ratings and reviews, verifying developer information, and being wary of apps that request excessive permissions upfront.
Downloading apps from reputable sources like the Google Play Store or the Apple App Store is the first line of defense against malicious or poorly designed apps. These app stores have security measures in place to screen apps for malware and other potential threats, but they are not foolproof. Before downloading an app, take the time to check its ratings and reviews. Pay attention to both the overall rating and the individual reviews. Look for patterns in the reviews that might indicate potential problems with the app, such as reports of excessive data usage, battery drain, or privacy violations. Verify the developer information to ensure that the app is being published by a legitimate company or individual. Look for a website or contact information for the developer. If the developer information seems suspicious or is missing, be wary. Be cautious of apps that request excessive permissions upfront. If an app requests a large number of permissions before you've even had a chance to use it, it may be a sign that it's collecting data unnecessarily. Consider whether the requested permissions are truly necessary for the app's functionality. Finally, keep your device's operating system and security software up to date. Security updates often include patches for vulnerabilities that could be exploited by malicious apps. By following these tips, you can minimize the risks associated with downloading new apps and protect your device and data from potential threats.
Using Permission Managers
Permission managers are third-party apps or built-in tools that offer enhanced control over app permissions. They can provide more granular control than the default settings, allowing you to customize permissions for individual apps based on your specific needs.
Permission managers are valuable tools for users who want more fine-grained control over app permissions than what's provided by default in Android or i OS. These tools can be either third-party apps or built-in features offered by some device manufacturers. One of the main benefits of using a permission manager is the ability to customize permissions for individual apps based on your specific needs. For example, you can allow an app to access your location only when you're actively using it, or you can prevent an app from accessing your contacts altogether. Some permission managers also offer advanced features such as the ability to create custom permission profiles for different apps or groups of apps. This can be useful if you have a set of apps that you trust more than others. Another advantage of using a permission manager is that it can help you identify apps that are requesting excessive or unnecessary permissions. Many permission managers provide a list of apps sorted by the number of permissions they request, making it easy to spot potential privacy risks. Some permission managers also offer real-time monitoring of app activity, alerting you whenever an app tries to access a sensitive permission. This can help you catch apps that are behaving suspiciously. However, it’s important to note that not all permission managers are created equal. Some third-party permission managers may themselves collect user data or contain malware. Therefore, it’s crucial to choose a reputable and trustworthy permission manager from a well-known developer. Before installing a permission manager, be sure to read the reviews and check its privacy policy.
Fun Facts About App Permissions
This section shares some interesting and surprising facts about app permissions. We'll explore unusual permission requests, the prevalence of data collection, and the ways app developers are innovating to work around permission limitations.
Did you know that some apps request permission to access your device's Bluetooth even when they don't seem to have any need for it? This is often used for location tracking, as Bluetooth beacons can be used to pinpoint your location indoors. Another fun fact is that the average smartphone user has over 80 apps installed, each with its own set of permissions. This means that the amount of data being collected about you on a daily basis is staggering. App developers are constantly innovating to find new ways to work around permission limitations. For example, some apps use techniques like "fingerprinting" to identify your device even if you've disabled location tracking. Fingerprinting involves collecting various pieces of information about your device, such as its operating system, hardware configuration, and installed fonts, to create a unique identifier. One of the most surprising permission requests is for access to your device's calendar. This permission can allow apps to track your appointments, meetings, and travel plans. Some apps even use this information to target you with personalized ads based on your schedule. The most commonly requested permission is for access to the internet. While this may seem harmless, it allows apps to send your data to remote servers, where it can be stored and analyzed. It's also interesting to note that some apps request permission to access your device's sensors, such as the accelerometer and gyroscope. This information can be used to track your movements and activities. By learning these fun facts about app permissions, you can gain a deeper appreciation for the complexity of app privacy and the importance of managing your permissions effectively.
How to Revoke Permissions on Android and i OS
This section offers step-by-step instructions on how to revoke permissions on both Android and i OS devices. We'll cover different versions of each operating system and provide screenshots to guide you through the process.
Revoking permissions on Android and i OS is a straightforward process, but the exact steps may vary depending on the version of your operating system. On Android, you can revoke permissions by going to Settings > Apps > [App Name] > Permissions. Here, you'll see a list of all the permissions that the app has requested. You can toggle each permission on or off to grant or deny access. On older versions of Android, you may need to go to Settings > Applications > Manage Applications > [App Name] > Permissions. On i OS, you can revoke permissions by going to Settings > Privacy. Here, you'll see a list of different types of permissions, such as Location Services, Contacts, and Camera. Tap on a permission to see a list of apps that have requested access to it. You can then toggle each app on or off to grant or deny access. It's important to note that revoking certain permissions may affect the functionality of an app. If you revoke a permission that is essential for the app to function properly, the app may not work as expected. However, in most cases, you can safely revoke permissions that seem unnecessary or suspicious without causing any problems. If you're not sure whether a particular permission is necessary, try revoking it and see if the app still works. You can always grant the permission again later if needed. It's also a good idea to regularly review your app permissions to ensure that you're not granting unnecessary access to your data. By following these steps, you can take control of your app permissions and protect your privacy on Android and i OS.
What If An App Still Accesses Data After Permission is Denied?
This section addresses a critical concern: what to do if an app appears to access data even after you've denied the relevant permission. We'll discuss potential causes, troubleshooting steps, and reporting mechanisms.
It's understandably concerning if an app continues to access data even after you've explicitly denied the relevant permission. While operating systems like Android and i OS are designed to prevent this, there are several potential reasons why it might happen. One possibility is that the app is using a workaround to access the data indirectly. For example, it might be using other permissions or sensor data to infer the information it's trying to access. Another possibility is that the app is caching data locally before you revoke the permission. This means that the app might still have access to previously collected data even after you've denied it further access. In some cases, the app might be exploiting a bug or vulnerability in the operating system to bypass the permission restrictions. If you suspect that an app is accessing data without your permission, there are several steps you can take. First, try restarting your device. This can sometimes clear cached data and resolve temporary glitches. Next, check the app's privacy policy to see if it describes how the app collects and uses data. If you believe that the app is violating its privacy policy or the operating system's permission rules, you can report it to the app store or the device manufacturer. You can also contact the app developer directly to report the issue. If you're still concerned about the app's behavior, you can try uninstalling it and finding an alternative app that respects your privacy. In extreme cases, you might consider using a firewall or other security tool to block the app's network access. However, this may also affect the app's functionality. It's important to remember that app permissions are not a foolproof guarantee of privacy. App developers can still find ways to collect data even if you've denied them certain permissions. Therefore, it's crucial to be vigilant about the apps you install and to regularly review your app permissions.
Listicle: Top 5 App Permission Mistakes to Avoid
This section provides a concise and memorable list of the most common app permission mistakes users make and how to avoid them. This format is designed to be easily shareable and digestible.
Here are the top 5 app permission mistakes to avoid: 1. Blindly Granting All Permissions: Avoid clicking "Allow" without reading the permission request. Take a moment to consider whether the permission is truly necessary for the app to function properly.
2. Ignoring Permission Updates: Pay attention to permission changes when you update an app. App developers may add new permission requests with updates, so it's important to review them.
3. Failing to Revoke Unnecessary Permissions: Regularly review your app permissions and revoke any permissions that seem unnecessary or suspicious.
4. Downloading Apps from Untrusted Sources: Avoid downloading apps from unofficial app stores or websites. These sources may contain malicious apps that can compromise your device and data.
5. Overlooking "While Using the App" Permissions: Be mindful of the "while using the app" permission option. This option allows apps to access certain features only when you're actively using the app, which can be a good compromise between granting full access and denying access altogether. To avoid these mistakes, adopt a proactive approach to managing your app permissions. Regularly review your permissions, be mindful of permission requests, and download apps only from trusted sources. By following these tips, you can protect your privacy and security on mobile devices.
Question and Answer
Here are some frequently asked questions about app permissions:
Q: What does "access to all files" mean on Android?
A: This permission grants the app broad access to all files stored on your device, including documents, photos, videos, and audio files. Granting this permission can pose a significant privacy risk, as the app could potentially access sensitive information without your knowledge.
Q: How can I tell if an app is tracking my location?
A: On both Android and i OS, you can see which apps have access to your location in the device's settings. Look for the location icon in the status bar, which indicates when an app is actively using your location.
Q: Is it safe to grant an app permission to access my contacts?
A: Granting an app access to your contacts can allow it to view and modify your contact list, as well as access information such as email addresses and phone numbers. Only grant this permission to apps that you trust and that have a legitimate need for it.
Q: What should I do if I suspect an app is misusing my data?
A: If you suspect that an app is misusing your data, report it to the app store or the device manufacturer. You can also contact the app developer directly to report the issue. Consider uninstalling the app and finding an alternative that respects your privacy.
Conclusion of Mobile App Permissions Guide: What Apps Can Really Access
Understanding app permissions is crucial for protecting your privacy and security in the mobile world. By being mindful of the permissions you grant, you can minimize the risk of data collection, targeted advertising, and potential security breaches. Remember to review your app permissions regularly, download apps from trusted sources, and be wary of apps that request excessive or unnecessary permissions. By taking these precautions, you can enjoy the convenience of mobile apps while safeguarding your valuable personal information.
Post a Comment