Phishing Email Examples: How to Spot and Avoid Online Scams
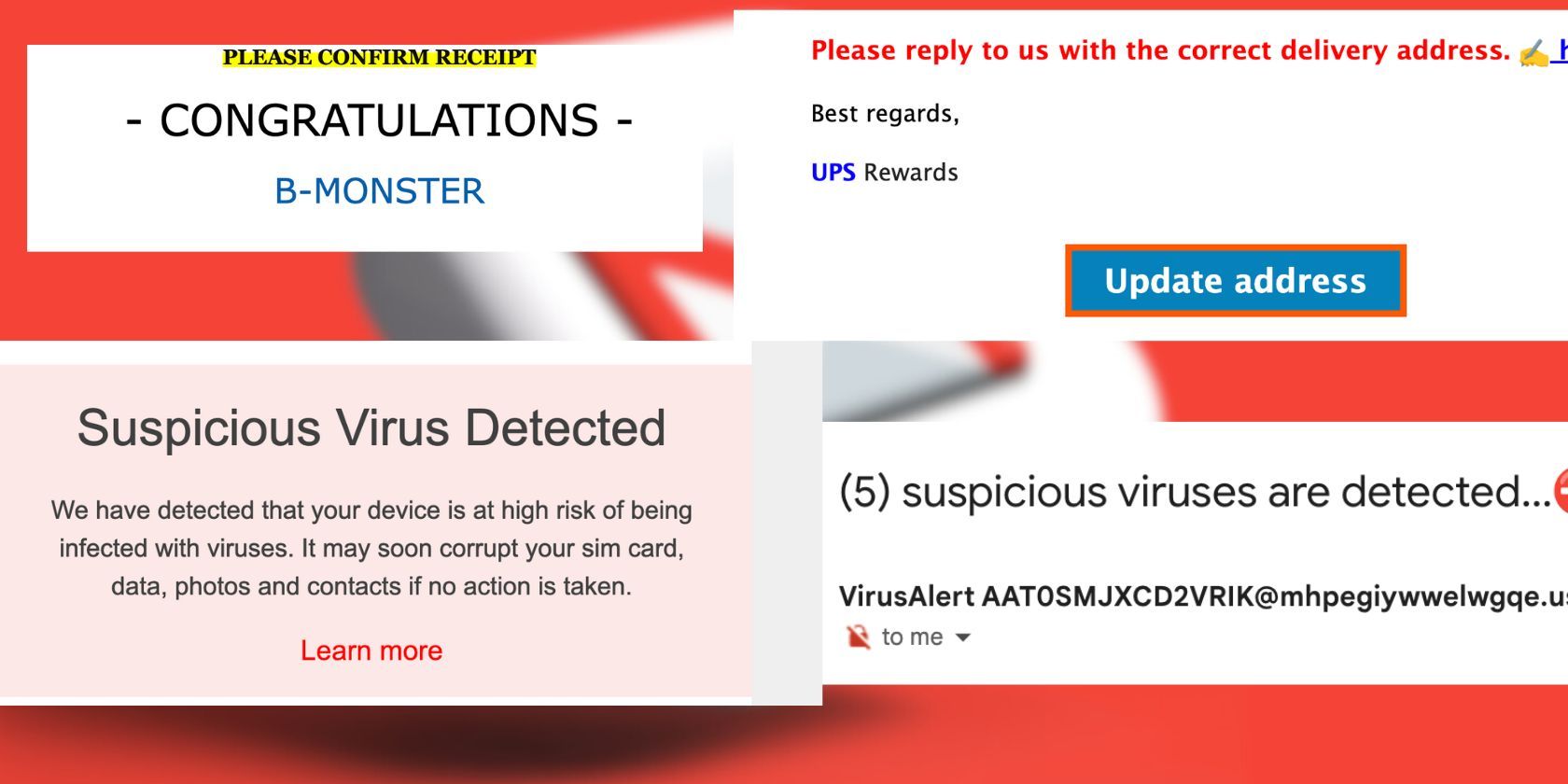
Ever gotten an email that just felt...off? Maybe it was the urgent tone, the slightly misspelled words, or the request for personal information that made your stomach churn. You're not alone. The world of online scams is vast and ever-evolving, with phishing emails being one of the most common and dangerous threats.
The sinking feeling of realizing you've been tricked, the worry about compromised accounts, and the sheer frustration of knowing someone is out there trying to steal your information can be incredibly unsettling. It's enough to make anyone feel vulnerable and question every email they receive.
This guide is designed to equip you with the knowledge and tools you need to identify and avoid phishing scams. We'll explore real-world examples, break down the key warning signs, and provide actionable steps you can take to protect yourself and your data. We will cover phishing email examples, how to spot them, and how to avoid them. This includes understanding common tactics, recognizing suspicious links and attachments, and knowing what to do if you suspect you've been targeted.
In this article, we'll delve into real-life phishing email examples, detailing how scammers craft their messages to appear legitimate. We'll explore telltale signs like grammatical errors, suspicious links, and urgent requests. You'll also learn how to verify email authenticity and what steps to take if you suspect you've received a phishing attempt. Mastering these skills will empower you to navigate the digital world with greater confidence and security, safeguarding your personal and financial information from malicious actors. This includes identifying common phishing tactics, understanding the psychological tricks used by scammers, and knowing how to report suspicious emails.
Real-World Phishing Email Examples
This section aims to illustrate what phishing emails actually look like in practice. I'll start with a personal anecdote. A few months ago, I received an email that looked like it was from my bank. The subject line was "Urgent: Account Security Alert." My heart skipped a beat. The email stated that there had been suspicious activity on my account and that I needed to verify my information immediately by clicking on a link. The design was almost identical to my bank's official emails, complete with their logo and branding. I was about to click the link, but something stopped me. I noticed a small grammatical error in the body of the email, and the link itself looked slightly different from the usual bank links I'd seen. Instead of panicking, I decided to log into my bank account directly through their website, not the link in the email. Thankfully, there was no suspicious activity. It was a phishing attempt, and I narrowly avoided falling for it.
This experience highlighted just how sophisticated these scams can be. They leverage our trust in familiar institutions and exploit our fear of losing money or having our accounts compromised. Phishing emails often mimic legitimate communications from banks, credit card companies, online retailers, or even government agencies. They may claim that your account has been suspended, that you have a pending refund, or that you need to update your personal information. The key is to always be skeptical and verify the authenticity of any email before clicking on links or providing personal information. Pay close attention to the sender's address, the grammar and spelling, and the overall tone of the message. If something feels off, it probably is. Phishing email examples often exploit current events, such as tax season or holiday shopping, to appear more relevant and believable.
Understanding Phishing Tactics
Phishing is a type of online fraud where criminals attempt to obtain sensitive information, such as usernames, passwords, and credit card details, by disguising themselves as a trustworthy entity. They typically do this through deceptive emails, websites, or text messages that mimic legitimate organizations. The goal is to trick victims into clicking on malicious links, downloading infected attachments, or providing their personal information on fake websites.
The success of phishing relies on manipulating human psychology. Scammers often use tactics such as creating a sense of urgency, appealing to authority, or exploiting fear and greed. For example, a phishing email might warn that your account will be suspended unless you take immediate action, or it might promise a large sum of money in exchange for your bank account details. These tactics are designed to bypass your critical thinking and encourage you to act impulsively. Phishing scams are constantly evolving, and scammers are always finding new ways to bypass security measures and trick unsuspecting victims. It's crucial to stay informed about the latest phishing techniques and to be vigilant about protecting your personal information. The best defense against phishing is knowledge and awareness. By understanding how phishing works and recognizing the red flags, you can significantly reduce your risk of becoming a victim. Remember, legitimate organizations will never ask you to provide sensitive information through email. Always verify the authenticity of any request by contacting the organization directly through a trusted channel.
The History and Myths of Phishing
The term "phishing" emerged in the mid-1990s, a play on the word "fishing," implying that scammers were casting out bait (emails) in hopes of "catching" victims' passwords and financial information. Early phishing attempts were relatively unsophisticated, often relying on blatant misspellings and poorly designed websites. However, as technology has advanced, so have phishing techniques. Today, phishing emails can be incredibly convincing, often indistinguishable from legitimate communications.
One common myth about phishing is that it only targets vulnerable or gullible individuals. In reality, anyone can fall victim to a phishing scam, regardless of their intelligence or technical expertise. Scammers are skilled at crafting persuasive messages that exploit our emotions and cognitive biases. Another myth is that phishing emails are always easy to spot. While some phishing attempts are obvious, others are remarkably sophisticated and can easily fool even the most discerning eye. Scammers are constantly updating their tactics to stay ahead of security measures and avoid detection. It's important to remember that phishing is a constantly evolving threat, and that staying informed and vigilant is the best way to protect yourself. Ignoring or dismissing potential phishing attempts is a dangerous gamble. Even if you think you're too smart to be tricked, it's always better to err on the side of caution and verify the authenticity of any suspicious email or website. The consequences of falling victim to a phishing scam can be devastating, ranging from financial loss to identity theft. Phishing email examples are prevalent in modern society.
The Hidden Secrets of Phishing
One of the most insidious secrets of phishing is the level of research and personalization that goes into some attacks. Scammers often gather information about their targets from social media, online databases, and even previous data breaches. This information is then used to craft highly targeted phishing emails that appear incredibly legitimate and relevant to the victim's interests or professional responsibilities.
For example, a scammer might impersonate a colleague or supervisor and send an email requesting sensitive information under the guise of an urgent work task. Or they might target individuals who have recently made online purchases, sending fake confirmation emails or delivery updates that contain malicious links. This level of personalization makes it much more difficult to distinguish between legitimate and fraudulent emails. Another hidden secret of phishing is the use of psychological manipulation. Scammers are experts at exploiting our emotions and cognitive biases to trick us into taking actions that we wouldn't normally take. They might create a sense of urgency, threaten negative consequences, or promise rewards or discounts to lure us into clicking on links or providing personal information. The key to avoiding these traps is to be aware of these psychological tactics and to approach every email with a healthy dose of skepticism. Always verify the authenticity of any request by contacting the sender directly through a trusted channel, and never click on links or provide personal information unless you are absolutely sure that the email is legitimate. Phishing email examples sometimes exploit our natural inclination to trust authority figures.
Recommendations for Avoiding Phishing Scams
The best way to avoid phishing scams is to be proactive and adopt a multi-layered approach to security. This includes educating yourself about the latest phishing techniques, using strong passwords, enabling multi-factor authentication, and keeping your software up to date.
Start by learning to recognize the common red flags of phishing emails, such as suspicious sender addresses, grammatical errors, and urgent requests for personal information. Be wary of emails that ask you to click on links or download attachments, especially if you weren't expecting them. Always hover over links to see where they lead before clicking on them, and avoid entering sensitive information on websites that don't have a secure connection (look for "https" in the address bar). In addition to being vigilant about email security, it's also important to protect your accounts with strong, unique passwords. Use a password manager to generate and store complex passwords, and never reuse the same password across multiple accounts. Enable multi-factor authentication (MFA) whenever possible. MFA adds an extra layer of security by requiring you to provide a second verification factor, such as a code sent to your phone, in addition to your password. This makes it much harder for scammers to access your accounts, even if they manage to steal your password. Finally, keep your software up to date. Software updates often include security patches that address vulnerabilities that scammers can exploit. Enable automatic updates to ensure that you always have the latest security protection. Being proactive with your security will make you a much harder target for phishing scams. Phishing email examples are always changing, so continuous education is vital.
Spotting Suspicious Links and Attachments
One of the most common ways phishing emails deliver their payload is through malicious links and attachments. It's crucial to develop the habit of scrutinizing these elements before clicking or downloading anything. When you hover your mouse over a link (without clicking), the actual URL will usually appear in the bottom left corner of your browser window. Compare this URL to the displayed text. Does it match the website you expect to be directed to? Look for discrepancies like misspellings, extra characters, or a completely different domain name. For example, instead of "bankofamerica.com," the link might lead to "bank0famerica.net" or a random string of characters. Similarly, be cautious of shortened URLs, as they can mask the true destination. If you're unsure about a link, it's always best to type the website address directly into your browser instead of clicking on the link in the email.
Attachments can be equally dangerous. Never open attachments from unknown or suspicious senders, even if the subject line seems legitimate. Common file types used for malicious purposes include .exe, .zip, .doc (with macros enabled), and .pdf. Even seemingly harmless files can contain malware that can infect your computer and steal your data. If you absolutely must open an attachment, scan it with a reputable antivirus program first. Keep your antivirus software up to date to ensure it has the latest protection against emerging threats. Consider using a virtual machine to open suspicious files in a safe environment that is isolated from your main operating system. This can prevent malware from infecting your primary computer. Always exercise extreme caution when dealing with links and attachments in emails, and when in doubt, err on the side of safety. Phishing email examples frequently contain these harmful elements.
Verifying Email Authenticity
Before taking any action on an email that asks for your personal information or directs you to a website, take a moment to verify its authenticity. Don't just assume that an email is legitimate because it looks official or comes from a familiar company. Scammers are experts at creating convincing imitations, so it's important to take a proactive approach to verification.
One of the easiest ways to verify an email is to contact the sender directly through a trusted channel, such as their official website or phone number. Don't use the contact information provided in the email itself, as this could be fake. Explain your concerns and ask if they actually sent the email in question. Most legitimate organizations will be happy to confirm or deny the authenticity of the email. Another way to verify an email is to check the sender's email address. Does it match the official domain name of the company or organization they claim to represent? Be wary of email addresses that use generic domains like @gmail.com or @yahoo.com, or that contain misspellings or extra characters. You can also use online tools to look up the sender's IP address and see if it matches the geographical location of the company or organization. If something seems suspicious, trust your instincts and err on the side of caution. It's always better to be safe than sorry when it comes to protecting your personal information. Phishing email examples are becoming increasingly sophisticated, making verification crucial.
What to Do If You Suspect You've Been Targeted
If you suspect that you've received a phishing email, don't panic. The first thing you should do is avoid clicking on any links or opening any attachments. Delete the email immediately, or mark it as spam to help your email provider identify and filter similar messages in the future. If you've already clicked on a link or opened an attachment, disconnect your computer from the internet to prevent any further communication with the scammer's server. Run a full scan of your computer with a reputable antivirus program to detect and remove any malware that may have been installed. Change your passwords for any accounts that you think may have been compromised, especially your email, bank, and social media accounts. Use strong, unique passwords and enable multi-factor authentication whenever possible. Monitor your bank accounts and credit reports for any signs of unauthorized activity. Report the phishing email to the organization that was being impersonated, as well as to the Federal Trade Commission (FTC) or your local law enforcement agency. Providing them with as much information as possible, such as the sender's email address, the subject line, and the content of the email, can help them track down the scammers and prevent others from falling victim to the same scam. Remember, early detection and swift action are crucial to minimizing the damage from a phishing attack. Phishing email examples require you to act quickly to protect yourself.
Fun Facts About Phishing
Did you know that the term "phishing" is believed to have originated from "fishing for passwords"? Or that the first recorded instance of phishing occurred in 1995, when hackers created a fake AOL account to steal passwords from other users? Phishing has come a long way since those early days, evolving into a sophisticated and lucrative criminal enterprise that affects millions of people worldwide.
Another interesting fact is that certain demographics are more likely to fall victim to phishing scams than others. According to research, younger adults (18-24) are more likely to click on phishing links than older adults (65+), possibly due to their greater reliance on technology and their tendency to trust online information. However, older adults are more likely to suffer financial losses from phishing scams, possibly because they have more assets to lose. Phishing attacks are also more likely to succeed on Mondays and Tuesdays, when people are more likely to be distracted and overwhelmed with work-related tasks. Additionally, phishing scams often spike during major events such as tax season, holiday shopping, and natural disasters, as scammers exploit people's heightened emotions and vulnerability. Despite the serious nature of phishing, there are some humorous aspects to it as well. Some phishing emails are so poorly written and riddled with grammatical errors that they are almost comical. However, it's important to remember that even the most absurd-looking phishing email can be dangerous, as it only takes one successful click to compromise your security. Phishing email examples are a reminder that vigilance is key.
How to Report Phishing Emails
Reporting phishing emails is a crucial step in helping to combat online scams and protect others from falling victim to the same attacks. By reporting phishing emails, you provide valuable information to organizations that can track down scammers, shut down fake websites, and prevent future attacks.
The easiest way to report a phishing email is to forward it to the organization that was being impersonated. For example, if you receive a phishing email that appears to be from your bank, forward it to the bank's security or fraud department. You can usually find their contact information on their official website. Many email providers also have built-in features for reporting phishing emails. In Gmail, for example, you can click on the "Report phishing" option in the drop-down menu next to the email. This will send the email to Google for analysis and help them improve their spam filters. You can also report phishing emails to the Federal Trade Commission (FTC) through their website, ftc.gov. The FTC uses the information you provide to track down scammers, identify trends, and educate consumers about how to avoid phishing scams. Finally, you can report phishing emails to your local law enforcement agency. They may be able to investigate the scammer and prosecute them if they are operating within your jurisdiction. Remember, reporting phishing emails is a collective effort that can help to make the internet a safer place for everyone. Even if you don't think your report will make a difference, it's always worth taking the time to submit it. Phishing email examples are a constant threat, and reporting them is a vital defense.
What If You Clicked on a Phishing Link?
Discovering you've clicked on a phishing link can be a moment of panic, but staying calm and acting quickly is essential to minimize the potential damage. The immediate next steps are crucial in containing the fallout.
First, disconnect your device from the internet immediately. This prevents the phishing site from potentially downloading malware or stealing data as you continue to browse. Next, run a full scan of your system with a reputable antivirus program. This will help identify and remove any malicious software that may have been installed. It's also wise to change all your passwords, especially for sensitive accounts like banking, email, and social media. Use strong, unique passwords for each account and consider enabling two-factor authentication for an added layer of security. Keep a close eye on your financial accounts and credit reports for any signs of unauthorized activity. Report the incident to your bank or credit card company immediately if you notice anything suspicious. You should also report the phishing attempt to the FTC and your local law enforcement agency. Providing them with details about the scam can help them track down the perpetrators and prevent others from falling victim. Depending on the severity of the situation, you may also want to consider freezing your credit reports to prevent identity theft. Remember, acting quickly and decisively is key to mitigating the damage caused by a phishing attack. Don't hesitate to seek professional help from a cybersecurity expert if you're unsure about what to do. Phishing email examples teach us the importance of rapid response.
Listicle: Top 5 Ways to Spot a Phishing Email
Navigating the digital world requires a keen eye for detail, especially when it comes to spotting phishing emails. Here are five key indicators that can help you distinguish a fraudulent message from a legitimate one:
- Suspicious Sender Address: Always examine the sender's email address carefully. Look for misspellings, extra characters, or a domain name that doesn't match the organization it claims to represent. Generic email addresses like @gmail.com or @yahoo.com should raise a red flag.
- Grammatical Errors and Typos: Phishing emails often contain grammatical errors, typos, and awkward phrasing. Legitimate organizations typically have professional writers and editors who ensure their communications are clear and error-free.
- Urgent or Threatening Language: Scammers often use urgent or threatening language to create a sense of panic and pressure you into taking immediate action. Be wary of emails that claim your account will be suspended or that you will face legal consequences if you don't respond immediately.
- Requests for Personal Information: Legitimate organizations will never ask you to provide sensitive information like your password, social security number, or credit card details through email. Be suspicious of any email that requests personal information, and always verify the authenticity of the request by contacting the organization directly.
- Suspicious Links and Attachments: Hover over links to see where they lead before clicking on them. Look for misspellings, extra characters, or a domain name that doesn't match the organization's website. Never open attachments from unknown or suspicious senders, as they may contain malware.
By keeping these five tips in mind, you can significantly reduce your risk of falling victim to a phishing scam. Stay vigilant, stay informed, and stay safe online. Spotting phishing email examples requires constant vigilance.
Question and Answer about Phishing Email Examples
Q: What's the biggest mistake people make when dealing with potential phishing emails?
A: The biggest mistake is acting impulsively without verifying the email's authenticity. People often click on links or provide personal information without taking the time to check for red flags, such as suspicious sender addresses or grammatical errors.
Q: How can I tell if a website is secure before entering my personal information?
A: Look for "https" in the address bar and a padlock icon. These indicate that the website uses encryption to protect your data. Be wary of websites that don't have these security features.
Q: What should I do if I accidentally gave my password to a phishing website?
A: Change your password immediately for any accounts that use the same password. Monitor your accounts for any signs of unauthorized activity and report the incident to the relevant organizations.
Q: Are mobile devices also vulnerable to phishing scams?
A: Yes, mobile devices are just as vulnerable as computers. Be cautious of phishing emails and text messages that target mobile users, and always verify the authenticity of any request before clicking on links or providing personal information.
Conclusion of Phishing Email Examples: How to Spot and Avoid Online Scams
Staying safe from phishing scams requires constant vigilance, education, and a proactive approach to security. By understanding the tactics used by scammers, recognizing the red flags of phishing emails, and taking steps to protect your personal information, you can significantly reduce your risk of becoming a victim. Remember to always verify the authenticity of any email before clicking on links or providing personal information, and report any suspicious emails to the relevant organizations. By working together, we can make the internet a safer place for everyone.
Post a Comment